SHODAN: Cracking IP Surveillance DVR
We have been continuing to play around with the SHODAN Computer Search Engine after first looking at it last week. We continue to identify a variety of devices we sometimes note on security engagements (although usually on internal networks) that should not be externally accessible and are either still using factory default credentials or are not using any credentials for access to administrative interfaces. Accessing the administrative panels of these devices would allow a bad actor to further compromise the organization running the device on its network. We can quantify that we are seeing results not just for poorly configured home offices or small businesses, but large and medium businesses who would experience significant negative effects when breached or their devices tampered with. We’ll continue to blog about our findings until we get bored with it. Today’s search demonstrates how we found a few hundred accessible interfaces for IP Camera DVR surveillance systems.
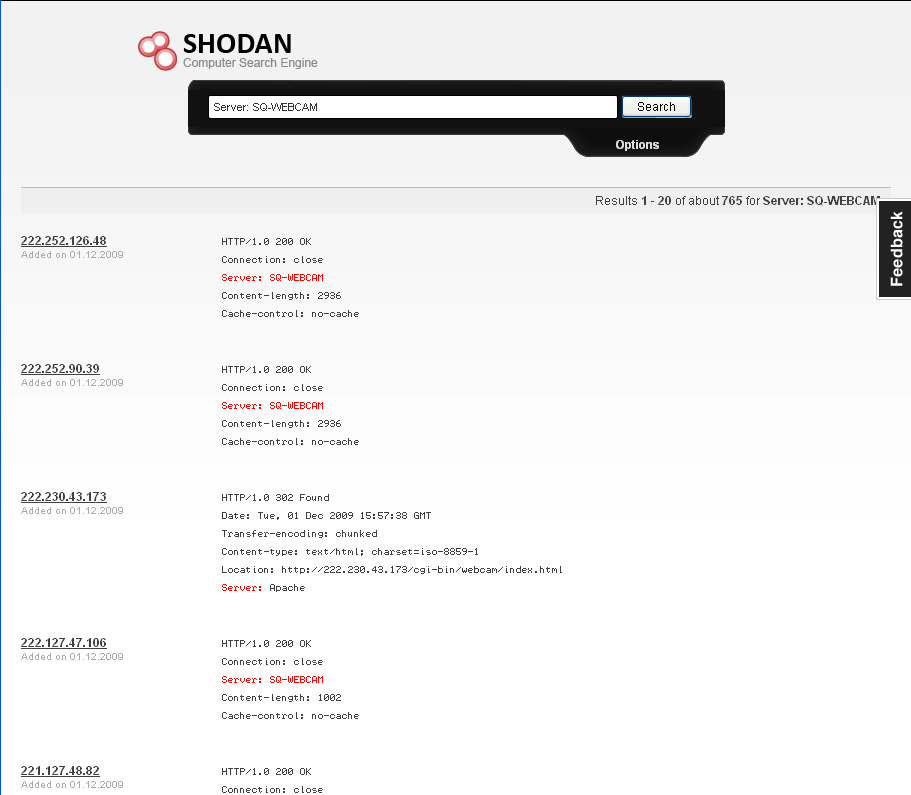
We start by browsing to SHODAN and performing a search for “webcam” and reviewing what shows up. This result catches our eye:
HTTP/1.0 200 OK
Connection: close
Server: SQ-WEBCAM
Content-length: 2936
Cache-control: no-cache
So we refine the search by only looking for “Server: SQ-WEBCAM“. 765 results, most with the format above (see screenshot at the bottom of the post).
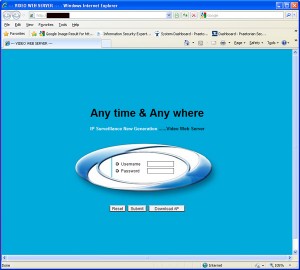
The IP address of most of the results opens up a login page as follows:
The particular IP in the example above is linked to a company that does bus sales and leasing in the Midwest. Some quick Google searching reveals that this login page is associated with the AVTech AVC 787 DVR (recording device for security cameras), pictured here.
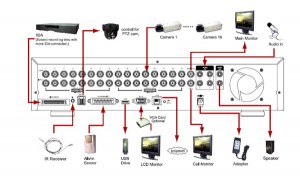
Having the model number allows us to find the device manual online a few seconds later. We first note an architecture diagram for how the security system is setup:
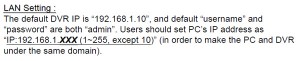
Then we find what we were looking for in the manual:
The Envelope Please
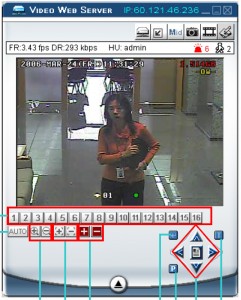
The majority of these surveillance systems are setup with the default id and password, we know that from experience. Once you are logged into the system as administrator, you can view a live feed or feeds, adjust the cameras position and zoom, play back recorded video, and if you wanted to coordinate a burglary you can go ahead and stop the devices recording. Here are some screenshots (taken from the product manual):
SHODAN Search is the same as Google Hacking?
There is someone out there who will say, “Yeah, but I could look at webcams with Google Hacking”. First, this is not a webcam, but let’s explore the thought anyhow. Let’s find a string related to the authentication page we want to find and Google it. We’ll use: “any time & any where ip surveillance new generation” “……video web server”. We retrieve 7 results, four different web sites, none the actual login page.
We try this search with SHODAN: “Server: SQ-WEBCAM”. 765 results returned, most are relevant. Even if both start by using spiders to find accessible hosts, the difference after finding that host is akin to the results of an NMAP scan on server characteristics being compared to what is essentially a search of server content found by a bot. Both are valuable tools, but they do not perform the same function.
Finally
We continue to hear some discussion of legal and ethical aspects to SHODAN. It is interesting, but it has to get past the level 0 discussion into more sophisticated arguments. We will note briefly that no cracking is demonstrated above, the screenshots are from a PDF manual and not anyone’s actual surveillance system.
We covered the legality question briefly in the first SHODAN post, the ethics question is murkier because it is a reflection of personal values for most people. We will state that if a device is Internet accessible, it is available to be scanned like a web page or anything else, the online equivalent of looking at something in plain view. If a device has no authentication mechanism, then it falls under that umbrella. Therefore in our opinion SHODAN is only efficiently displaying what is already in plain view. It changes the game in doing that because it magnifies the ability to identify poorly configured environments visible by external scan, but the activity at its atomic level (an NMAP style scan) was already an available technique.
If a device has a poorly configured authentication mechanism, or is still using a factory default id and password, this is irresponsible but accessing the service through the authentication is logically different than performing a perimeter scan.
Companies should and sometimes do advise people to change the factory default authentication on the devices they sell. Sometimes the setup mechanisms force a password change. Better mechanisms exist that avoid using common defaults, however they add complexity to the sales process. An IT professional who has the experience to know the proper way to set devices up, but sets up these devices without changing the default credentials is not exercising due care in his or her profession. A company that allows a person who does not have the requisite experience to set up such systems is also not exercising due care. Should they be the victim of cybercrime because of it? Of course not, but they are still acting foolishly, lazily, or both, and because of it are being irresponsible with both their own resources and the data they collect from customers and stakeholders.
Just One More Thing…
In a conversation with the creator of SHODAN, he mentioned that he will be setting up a Googledorks style page where people can contribute the results of searches and vulnerabilities. When that’s up, we anticipate a number of other search types contributed by the security community coming to light right alongside the vulnerabilities inherent in the devices showing up in the results. This example isn’t really a vulnerable service in the idea that an exploit would be required though, this is just an example of hundreds of poorly configured devices with weak security by default settings.
We also note today the following update from SHODAN: “Updated the index, now with 4x more data. Let me know through Twitter which services/ ports you would like to have indexed.”
Contribute some of your searches or ideas in the comments of the blog, we want to see what creative results people are coming up with.