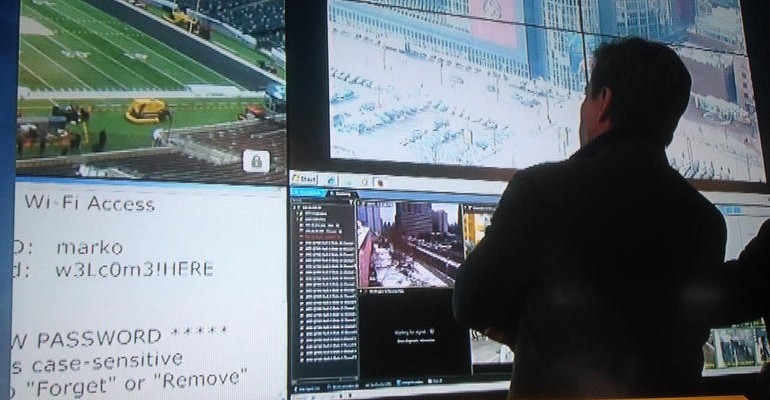
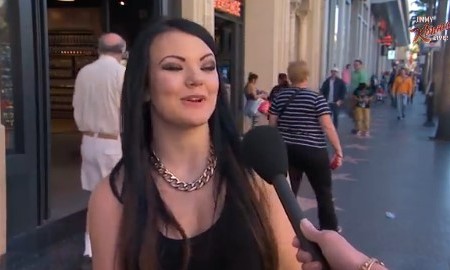Jimmy Kimmel Gets your Password
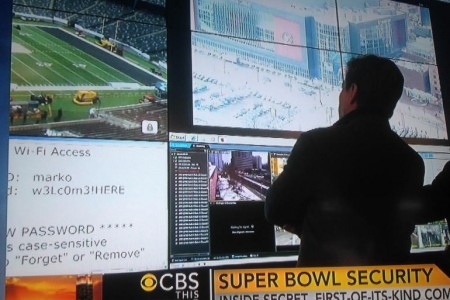
It didn’t take a whole lot of social engineering for people to give up their passwords: ask them what the password consists of (like it’s my cat’s name and birthday), ask the cat’s name, ask a deflecting question, then ask for the birthday.